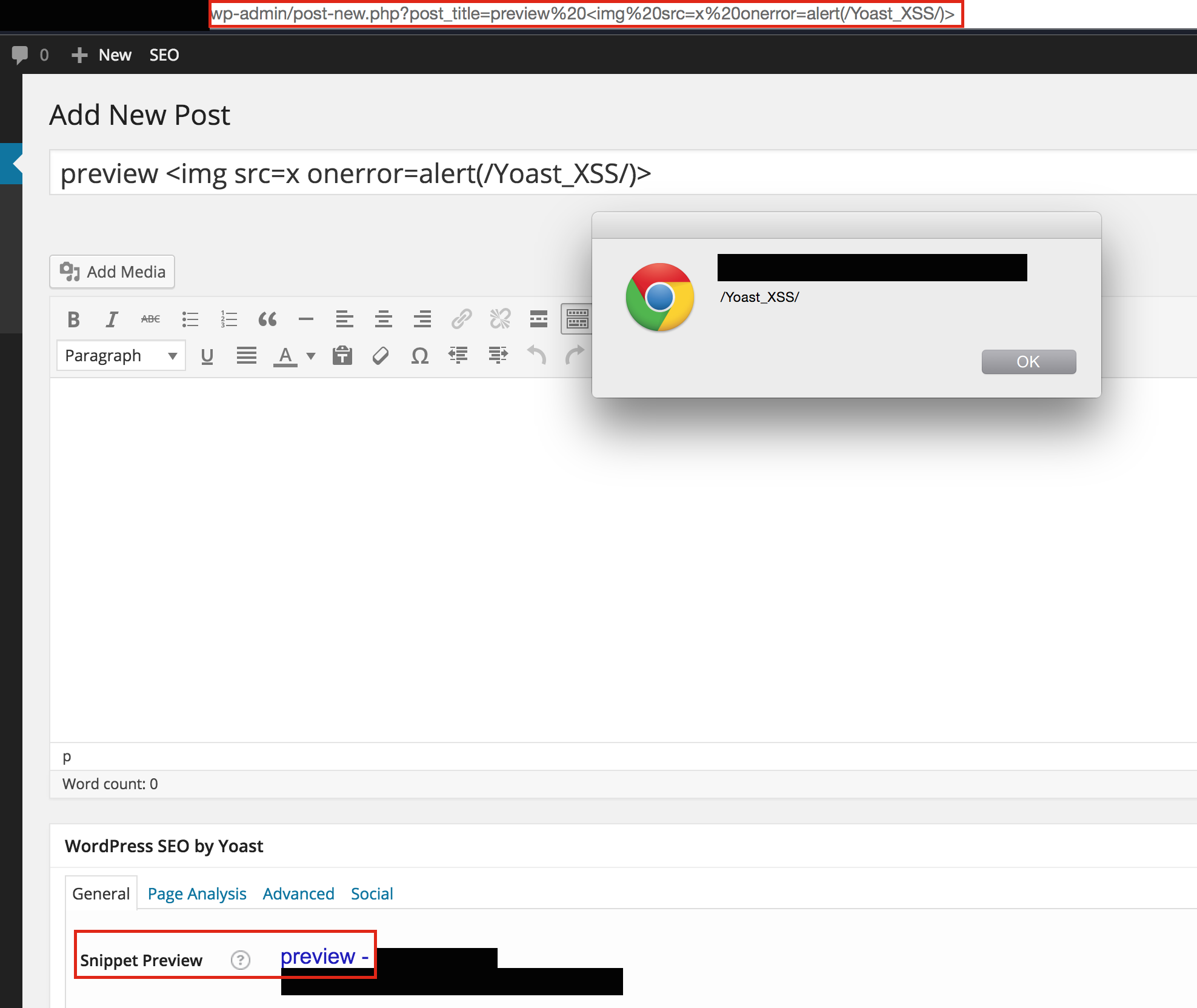
Anyone who read my post yesterday is probably confused by 1) this domain name and 2) my mention of it being my “first post”. This blog is a reboot of my previous site (where the older posts came from). I’m starting over in hopes that it will incentivize me to take blogging seriously again. This post will explain my plans for this blog, and with any luck, convince you to come along for that ride. I had imagined writing a longer and more thoughtful introduction, but events have conspired to force my hand. When in doubt, start.