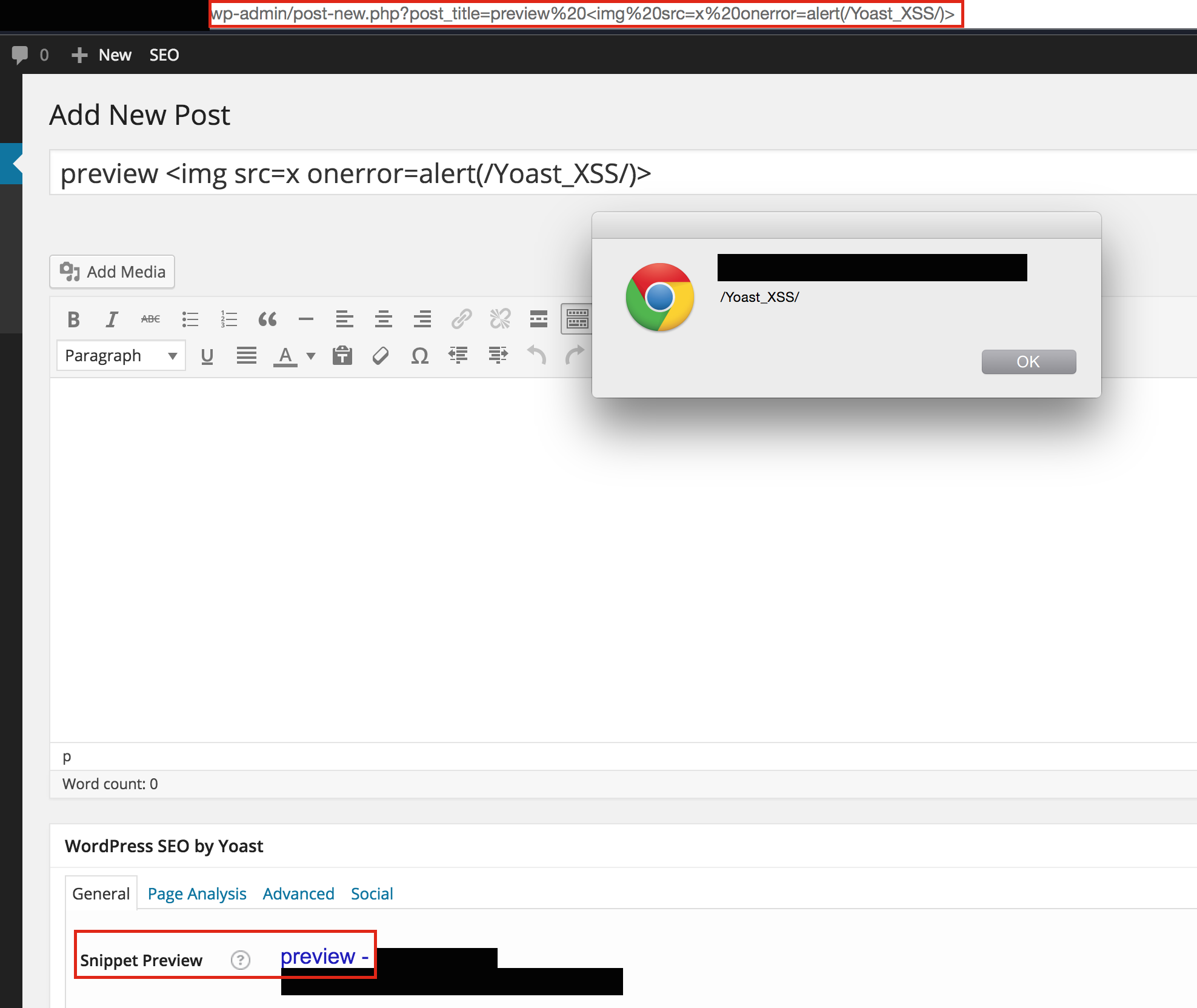
The AddToAny Share Buttons WordPress Plugin was, until recently, vulnerable to a DOM-based cross-site scripting issue. The file in question is hosted on the author’s site, so you’re not vulnerable anymore (you’re welcome). If you just want the vulnerability details, go here . Now for the story of this bug.
This particular journey started with an email from XSSposed , a site intended to allow security researchers to responsibly report cross-site scripting issues in sites that don’t run formal bug bounty programs like those seen here . Having never heard of it before, I was immediately suspicious. I like the concept of bug bounties just fine, but I was a little surprised to learn that I had unknowingly opened one on my site.